What are the NDMO Standards?
As part of the Vision 2030 initiative, the Kingdom of Saudi Arabia (KSA) adopted the National Data Management and Personal Data Protection Standards, a framework designed to secure sensitive government information, ensure public trust, and govern data management across its public entities.
Developed by the National Data Management Office (NDMO), the Kingdom’s national regulator, the Standards are designed to protect personal and government data, defined as:
- Personal Data | Any element of data, alone or in connection with other available data, that would enable the identification of a Saudi citizen.
- Government Data | Raw data or processed data that is received, produced or held by public entities, regardless of the source, form or nature.
To Whom do the NDMO Standards Apply?
The NDMO Standards apply to all Public Entities within the Kingdom of Saudi Arabia, as well as to all “business partners handling government data.” These business partners are responsible for applying the Standards to all government data within their jurisdiction.
The Standards cover government data in any and all its forms:
- Paper records
- Emails
- Data stored in electronic form
- Voice recordings
- Videos
- Maps
- Photos
- Scripts
- Handwritten documents
Or any other form of recorded data.
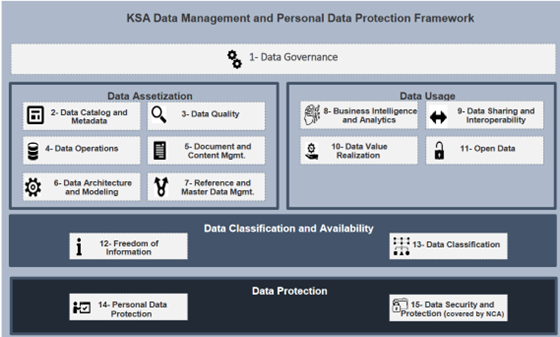
The 15 Domains
The Data Management and Personal Data Protection Standards document defines the requirements for 15 domains. They are summarized as follows:
- Data Governance
Authority over the planning of the organization’s data management practices via people, processes, and technologies. - Data Catalog and Metadata
Enabling effective access to high-quality integrated metadata. - Data Quality
Improving the quality of the organization’s data until it is fit for the customer’s requirements. - Data Operations
Maximizing data value throughout its lifecycle via optimized data storage measures. - Document and Content Management
Governs the capture, storage, access, and use of content stored outside of relational databases. - Data Architecture and Modelling
Establishing structures to ensure end-to-end data processing across (and within) entities. - Reference and Master Data Management
Establishes a common point-of-reference for all critical data by linking it to a single master file. - Business Intelligence and Analytics
Analyzes the organization’s data to draw insight and form conclusions. - Data Sharing and Interoperability
The collection of data from different sources and integrated solutions that facilitate harmonious communication between various IT components. - Data Value Realization
Continuously mining data to find opportunities for cost savings or revenue generation. - Open Data
Organizational data which, if made public, could foster economic growth, speed innovation, or improve transparency. - Freedom of Information
Providing Saudi citizens with a way to access government information, know how to access government information, and file an appeal in the event of a dispute. - Data Classification
Categorizing data so that it may be used and protected efficiently. Data Classification levels are assigned based on the potential damage caused by the compromise or mishandling of said data. - Personal Data Protection
Protecting a Saudi citizen’s right to having their personal data handled and protected properly. - Data Security and Protection
The methods employed (people, processes, technology) to secure an entity’s data. This particular domain is mandated by the Saudi National Cybersecurity Authority.
Guiding Principles
Per the Document, the Standards are anchored in the following eight Guiding Principles, which underscore the 15 domains outlined above. They are summarized as:
- Data as a National Asset | Government data should be discoverable and protected, with the potential to be monetized.
- Data Protection by Design | Build proactive processes that protect individual’s privacy and their right to consent/refuse under KSA laws.
- Open by Default | Ensure most government data is available by default, unless non-disclosure is sufficiently justified.
- Ethical Data Use | Build ethical data practices around fairness, traceability, and contribution to the “Common Good.”
- Purposeful Design | Adopt human-centric data usage, collection, processing, and sharing processes.
- Data-Driven Outcomes | Build a Next-Generation Public Sector where decisions are based on data insights.
- Learning Culture | Ensure that Saudi talent is growing sufficiently to fill competitive market and data management needs.
- Trusted Data | Build trust between the government and the public by ensuring data security or being transparent about the level of data security.
Compliance and Enforcement
Covered entities must complete a compliance audit once a year and return the results to the NDMO in the third quarter. The NDMO will then consolidate and publish the results to stakeholders at the entity, sector, and government level.
At each level of specification, a binary 100% or 0% will be assigned – either a pass or a fail. Leading the compliance audit will be Chief Data Officer, and evidence will be supplied in the report to support scores where applicable.
Based on the results of the audits, the NDMO reserves the right to perform additional ad hoc audits on selected entities as necessary.
Pillars of the Data Lifecycle
The Standards are designed to protect data across its lifecycle. That lifecycle is divided into five key stages.
Credit: NDMO Data Management and Personal Data Protection Standards document.
The Necessity of NDMO Data Classification
Data Classification is of particular importance to the overall goal of maintaining processes in which sensitive public data can be secured.
Classification Requirements
Security standards need to be enacted based on how important the information is, or in other words, how much damage will be caused should that particular piece of data be compromised. This is ascertained and accomplished via Data Classification.
As the Standards state, “Data Classification involves the categorization of data so that it may be used and protected efficiently. Data Classification levels are assigned following an impact assessment determining the potential damages caused by the mishandling of data or unauthorized access to data.”
They further detail how each Entity must register a list of all identified assets in the process of Data Classification. That register needs to include:
- A list of identified assets.
- Classification levels assigned to each asset.
- The dates those classification levels were assigned.
- The amount of time those classifications stand.
- Classification levels approved during review.
- The dates of the classification levels’ review.
Data Classification Process
To accomplish the above Data Classification designs, a structured Data Classification process needs to be in place. Practitioners must:
- Identify all the entities’ data.
- Assign the parties responsible for performing Data Classification.
- Conduct the impact assessment process.
- Identify the category impacted (national interest, organizations, individuals, environment, etc.)
- Determine the level of impact (high, medium, low, or none).
- Consider compliance with existing regulations (only if the impact is “low”).
- Assess the benefits of disclosure against the potential negative impacts (only if there are not compliance consequences for disclosing the data).
- Review the classification level once last time for completeness and accuracy.
- Apply the relevant controls.
This process is important because security needs to be balanced with resources and a user-friendly environment. Establishing which pieces of data need the most stringent (and often resource-heavy, time-consuming) controls both lets you put the maximum amount of security fire power in those places and spare other forms of data from having unnecessarily weighty policies.
Fortra's Data Classification
Fortra’s Data Classification Suite (DCS) solution helps teams in both the public and private sectors accomplish their compliance goals.
Armed with powerful context-based classification, Fortra DCS combines:
- Pattern matching
- Machine learning categorization
- Automated PII detection
For protection that extends beyond labeling alone, organizations can leverage Fortra's Data Classification to inform their people and their policies of which data needs to be secured, and how to do so. To enable this, metadata attributes are embedded into emails, files, and documents at every stage of the content lifecycle, with visual cues applied automatically to delineate compliance-sensitive content.
Key benefits include:
- Protection for expanded file types, including JPGs, PDFs, and more.
- Integration with the tools your team uses every day, whether in Windows or Mac environments.
- The ability to secure a wide range of file shares on-premises or in the cloud.
- A flexible policy engine that supports custom conditions for each organization.
- Files enriched with DCS-applied metadata that better inform downstream services like Fortra’s Secure Collaboration, CASB, and DLP.
And more, including unique differentiators that set Fortra DCS apart from the competition. Those include:
- Special HIPAA Compliance | Billing data cannot be shared with other departments like nursing, IT, or operations.
- Unique Banking Protection | Banking is barred from sharing with Brokerage in the same organization to prevent SEC infractions.
- Stringent GDPR Security for PII | Data originated within the EU is blocked by our DLP solution from entering restricted geographies.
- No Retention Report Liability | Sometimes retention reports are generated to clean data, necessarily using paid storage and putting the organization at risk. Our DCS solution helps prevent this occurrence.
Data Classification is just one of the many ways in which the Saudi NDMO National Data Management and Personal Data Protection Standards ensure public data is properly protected for tomorrow. But it is one of the most crucial when given its vital role within the broader data protection context.
Learn more about the NDMO Standards and discover additional data protection solutions from Fortra.