Understanding the Saudi NDMO Standards
As governments find themselves switching fully to digital methods, it becomes time to definitively establish the rules of the security game. The Kingdom of Saudi Arabia’s (KSA’s) National Data Management and Personal Data Protection Standards are designed to do just that, setting for the cybersecurity practices that will safeguard public and government-owned data as part of the Vision 2030 initiative.
These standards were created and are implemented by the National Data Management Office (NDMO), the Kingdom’s national regulator, and will be referred to as the NDMO Standards, or simply the Standards in the course of this blog.
To Whom do the NDMO Standards Apply?
The NDMO Standards apply to all KSA Public Entities and business partners handling government data. Per the official documentation, those parties are responsible for protecting both personal and government data, defined as:
- Personal Data | Any element of data, alone or in connection with other available data, that would enable the identification of a Saudi citizen.
- Government Data | Raw data or processed data that is received, produced or held by public entities, regardless of the source, form or nature.
And the rules apply to government data in “any form of recorded data,” including paper records, handwritten documents, emails, maps, and more.
What Are the 15 Domains?
The Standards define the requirements for 15 specific domains, namely:
- Data Governance
- Data Catalog and Metadata
- Data Quality
- Data Operations
- Document and Content Management
- Data Architecture and Modelling
- Reference and Master Data Management
- Business Intelligence and Analytics
- Data Sharing and Interoperability
- Data Value Realization
- Open Data
- Freedom of Information
- Data Classification
- Personal Data Protection
- Data Security and Protection
For a more in-depth explanation of these domains, see here.
What Role Does Data Classification Play?
Data Classification, in addition to being domain #13, is also a key pillar of the data lifecycle, which the Standards are designed to protect. Those pillars of the data lifecycle are illustrated in the image below:
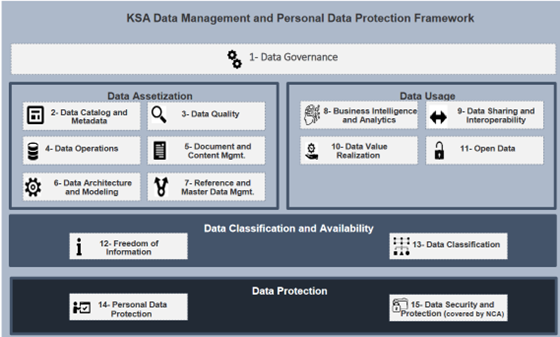
Credit: NDMO Data Management and Personal Data Protection Standards document.
They are:
- Data Governance: The overarching rules that will dictate subsequent data management processes, policies, and procedures.
- Data Assetization: The process of assigning value to data based on characteristics like function and quality.
- Data Usage: How data is being utilized within the organization; in this case, the government.
- Data Classification and Availability: Making data available to Saudi citizenry and sorting it based on how crucial its safety is to Saudi national security, government stability, and other factors.
- Data Protection: The obligation to protect Saudi personal and government information, and the means by which to do so.
The Requirement to Classify Data
The Standards state, “Data Classification involves the categorization of data so that it may be used and protected efficiently. Data Classification levels are assigned following an impact assessment determining the potential damages caused by the mishandling of data or unauthorized access to data.”
In other words, classifying data correctly is integral to properly securing it. One classifies data based on the negative impact it would have on the organization if that data were to be breached – then you divvy out the appropriate level of controls from there.
The NDMO Standards require that a register be made of all identified assets in the course of Data Classification. Mandated in the register are:
- A list of identified assets.
- Classification levels assigned to each asset.
- The dates those classification levels were assigned.
- The amount of time those classifications stand.
- Classification levels approved during review.
- The dates of the classification levels’ review.
Data Classification Process
To accomplish the above Data Classification designs, a structured Data Classification process needs to be in place. Practitioners must:
- Identify all the entities’ data.
- Assign the parties responsible for performing Data Classification.
- Conduct the impact assessment process.
- Identify the category impacted (national interest, organizations, individuals, environment, etc.)
- Determine the level of impact (high, medium, low, or none).
- Consider compliance with existing regulations (only if the impact is “low”).
- Assess the benefits of disclosure against the potential negative impacts (only if there are not compliance consequences for disclosing the data).
- Review the classification level once last time for completeness and accuracy.
- Apply the relevant controls.
This process is important because security needs to be balanced with resources and a user-friendly environment. Establishing which pieces of data need the most stringent (and often resource-heavy, time-consuming) controls both lets you put the maximum amount of security fire power in those places and spare other forms of data from having unnecessarily weighty policies.
Fortra's Data Classification
Fortra’s Data Classification Suite (DCS) solution helps teams in both the public and private sectors accomplish their compliance goals.
Armed with powerful context-based classification, Fortra DCS combines:
- Pattern matching
- Machine learning categorization
- Automated PII detection
For protection that extends beyond labeling alone, organizations can leverage Fortra Data Classification to inform their people and their policies of which data needs to be secured, and how to do so. To enable this, metadata attributes are embedded into emails, files, and documents at every stage of the content lifecycle, with visual cues applied automatically to delineate compliance-sensitive content.
Key benefits include:
- Protection for expanded file types, including JPGs, PDFs, and more.
- Integration with the tools your team uses every day, whether in Windows or Mac environments.
- The ability to secure a wide range of file shares on-premises or in the cloud.
- A flexible policy engine that supports custom conditions for each organization.
- Files enriched with DCS-applied metadata that better inform downstream services like Fortra’s Secure Collaboration, CASB, and DLP.
And more, including unique differentiators that set Fortra DCS apart from the competition. Those include:
- Special HIPAA Compliance | Billing data cannot be shared with other departments like nursing, IT, or operations.
- Unique Banking Protection | Banking is barred from sharing with Brokerage in the same organization to prevent SEC infractions.
- Stringent GDPR Security for PII | Data originated within the EU is blocked by our DLP solution from entering restricted geographies.
- No Retention Report Liability | Sometimes retention reports are generated to clean data, necessarily using paid storage and putting the organization at risk. Our DCS solution helps prevent this occurrence.
Data Classification
Data Classification is just one of the many ways in which the Saudi NDMO National Data Management and Personal Data Protection Standards ensure public data is properly protected for tomorrow. But it is one of the most crucial when given its vital role within the broader data protection context.
Learn more about the NDMO Standards here and discover additional data protection solutions from Fortra.

